Utility companies have a dangerous road ahead when it comes to cybersecurity. The 2022 State of Reliability report issued by the North American Electric Reliability Corporation (NERC) warns of an “unprecedented and relentless” security threat landscape.
The threats faced by utility companies come from new vulnerabilities in software, cybercriminals looking for a ransom payout, state-sponsored hacking groups, “hacktivists,” and more.
Just a few of the referenced recent supply-chain attacks that impacted energy companies include suppliers like SolarWinds, Microsoft Exchange, Pulse Secure, and Kaseya.
The key types of cyber threats faced by large, medium, and small utility companies are:
- Supply chain attacks
- Geopolitical threats
- Ransomware
- Domestic extremists
- Drones
- COVID-19
Small and mid-sized utility companies are particularly challenged when it comes to improving cyber defenses to address these threats. They typically have fewer resources than larger utilities, so they have to budget carefully and prioritize cybersecurity activities. They are also tightly regulated, and can’t simply charge customers more to help pay for the need for stronger security.
One of the ways these smaller energy facilities can improve their security posture affordably is through a proactive vulnerability management program. Vulnerability assessment and management is a process of scanning all assets in a facility, identifying vulnerabilities, prioritizing those threats, and then removing them.
Vulnerability management doesn’t have to be expensive when you automate the process rather than try to manage it manually. For example, you can have assets monitored and scanned on a schedule and have threats immediately identified and prioritized for you. Automated tools can also provide recommendations for the mitigation of threats.
One such tool that does all this for you is CyberWizPro. It levels the playing field for small and mid-sized utility companies by helping them improve cybersecurity without a large cost burden.
Approximately 60% of data breach victims can trace the incursion back to an unpatched system vulnerability. Even more (62%) say that their organization wasn’t aware of the vulnerability prior to the breach.
Following is how small & mid-sized electrical industry companies can use vulnerability management to affordably improve their security defenses.
Vulnerability Management Steps for Smaller Utilities
Determine the Scope
First, you will want to determine the scope of your vulnerability management process. This can include profiling systems into classes, such as Windows network systems (e.g., domain controllers, mail servers, database servers, etc.), mobile devices, and more.
Plan Your Vulnerability Lifecycle Process
Vulnerability management is not a “one-and-done” exercise that’s undertaken once in a blue moon. It’s important for any size utility company to have an ongoing vulnerability lifecycle process in place.
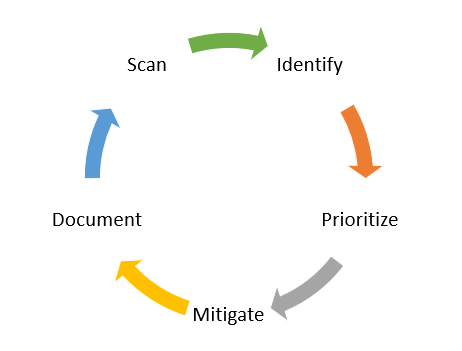
Plan out a continuous lifecycle where systems are monitored. The lifecycle would look something like this:
- Scan
- Identify
- Prioritize
- Mitigate
- Document
Put an Automated Vulnerability Management Tool in Place
One reason that small and mid-sized utilities don’t have a vulnerability management program is that they lack the staff or resources to do it manually.
Putting an automated vulnerability management system, like CyberWizPro, in place significantly speeds up the process and eliminates all the time-consuming manual tasks. It won’t require additional personnel or take time away from other vital security tasks.
Scan Network & Identify Vulnerabilities
Once the tool is in place, it can automatically detect endpoints and other assets and scan them all for any vulnerabilities. This uncovers those hidden threats that often lurk in mission-critical infrastructure networks so they can be addressed before they result in a breach.
Prioritize Vulnerability Mitigation
Prioritizing found vulnerabilities is an important step in your vulnerability management process. It’s not usually feasible to tackle all vulnerabilities at once, prioritization helps you identify which are the more severe and wide-reaching so they can be addressed first.
If using a tool like CyberWizPro, this prioritization is done for you, and suggestions are provided for mitigation.
Mitigate Threats Through Patching & Other Remediation Tactics
Next is mitigation of the threats, which will usually involve patching/updating the affected system. IT technicians may also decide to separate certain systems from others to ensure a vulnerability doesn’t impact a larger part of the entire network.
Another method is to designate a test group and push patches to that small group first. If no adverse effects are detected, then the update is pushed out to all over the next day or two.
Certain systems for energy such as SCADA systems can’t be patched automatically. That is a separate process.
Document Vulnerability Management Activities
Document the vulnerabilities that were found, where they were found, and what steps were taken to remove them. It’s important to keep a record of vulnerability management activities for compliance and forensic reasons.
Continually Monitor for New Threats
Continuous monitoring should be in place to identify any new vulnerability risk. For example, vulnerabilities can be introduced when new software is installed, existing software is updated, or when new hardware is connected to a network. All these activities should be flagged, and vulnerability monitoring and assessment should be an ongoing function.
Learn How Easy & Affordable Vulnerability Management Can Be
CyberWizPro is an affordable and effective option for vulnerability assessment and management.

