One of the facts of life when running a small or medium business (SMB) is that cybersecurity is going to need to be a priority. In addition to marketing, converting leads, and managing your employees, you need to ensure your digital systems stay clear of data breaches.
Just one data breach causes an average of 60% of small businesses to close their doors for good within six months of the incident. The high costs involved go far beyond physically remediating the breach. Lost business, lost customer trust, and litigation are just some of the additional costs.
One of the best ways that SMBs can stay on top of cybersecurity is to put a vulnerability management process in place. This is a continuous process of scanning all digital assets for vulnerabilities, identifying them, and mitigating them to improve overall cybersecurity.
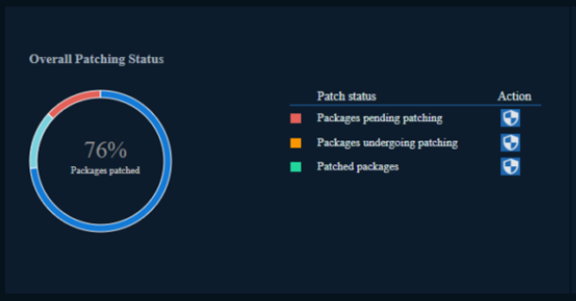
76% of all applications have at least one vulnerability.
Having a process to manage vulnerabilities isn’t just something that larger enterprises need to worry about. Small and mid-sized companies are often targeted more by cybercriminals because they are usually easier to hack. Many of them don’t keep up with assessing vulnerabilities, employee training, access controls, and other best practices of network security.
The lack of time, money, knowledge, and resources are often reasons given for SMBs to lack necessary vulnerability management. However, this can be remedied by finding good software designed to manage the vulnerability lifecycle for you.
The most important benefit that vulnerability management software can bring to the table is to reduce the need for additional personnel and extensive training on identifying and prioritizing vulnerabilities. An automated tool for managing vulnerabilities can greatly reduce the cost and time commitment needed to run an effective program.
However, not all software claiming to be a vulnerability assessment and management tool are created equally. Some are difficult to use, others lack comprehensive reporting.
Following, are some tips on the important factors you should consider when choosing the best vulnerability management tool for your small or mid-sized business.
Scanning
A good vulnerability management tool should be able to scan all assets in your network easily. Vulnerabilities can be present in any type of software, whether it is used to run an operating system, application, hardware device, or cloud-based platform.
Look for tools that will show scanning progress, so you know at a glance how many assets have been assessed and how many are left to review. Good tools for vulnerability assessment also have the ability to detect the endpoints that need to be scanned automatically, which saves your IT team a lot of time.
Patching
The remedy for vulnerabilities is to patch them with a “fix” that has been issued by the software developer. There are hundreds of these to review in any given month to address hundreds of vulnerabilities. You want a system that does all that patching work automatically and provides you with a progress update.
Ease of Use
SMBs need software that doesn’t have a huge learning curve. Many want a “just plug it in and it works” experience, which is necessary because time and resources are limited. They don’t have the capacity to entertain a difficult system that is going to take weeks of training for their team.
Look for a vulnerability management system that is simple to use and requires minimal training or configuration.
Reporting
The need to report on cybersecurity activities is shared by all organizations, no matter the size. SMBs need to adhere to data privacy policies and regulations just as larger organizations do.
Make sure you have the ability to get the reports you need from a vulnerability management tool. You may not know what you’ll need two years from now, so it’s important to also look for the ability to customize reports for your needs.
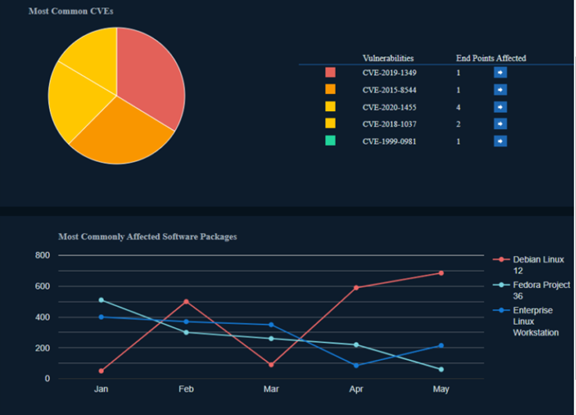
Reporting should be visually engaging, not just the data presented in a table view. It should also be intuitive and provide the types of insights that aid timely decision-making.
Endpoint Installation
Some vulnerability management solutions require you to install an agent on each endpoint. This can cause multiple problems that negatively impact security and productivity. For example:
- The agent may slow down devices
- The agent may be incompatible with some devices
- A device may get missed, which can lead to undetected vulnerabilities
- It can be a hassle getting the agent installed on all employee devices
Look for a vulnerability lifecycle management tool that doesn’t require endpoint installation. It should be able to detect endpoints through their connectivity to the network and have the ability to scan them without an agent being installed.
Try a Vulnerability Solution that Checks All the Boxes
CyberWizPro by WizNucleus is an easy-to-use vulnerability management software that gives you superior performance for an affordable price.

