When you think about all the different devices connected to a corporate network, managing their vulnerabilities can seem complex, but manageable. Then add on top of that software, cloud applications, and network hardware, and the task can seem incredibly daunting.
Vulnerabilities are a fact of life when working in any type of technology environment. Software, firmware, and operating systems get updated. Those updates often contain code flaws that can be exploited. These vulnerabilities can also exist in new devices and apps.
During the first half of 2022, disclosures of IoT device vulnerabilities increased by 57% compared to the last half of 2021. It was also found that 71% of them have a “high impact” on system and device availability.
Organizations and mission-critical facilities need to manage these vulnerabilities if they want to reduce the risk of a network breach. But this doesn’t have to be hard or complicated.
Breaking down vulnerability management into simple steps, and using vulnerability tools that automate most of those steps, can make the entire process easy and efficient.
What Makes Managing Network Vulnerabilities Hard?
Before we get into simplifying your vulnerability management strategy, let’s look at the barriers people have. What makes them think that assessing and handling vulnerabilities is difficult?
- There is not enough time to handle it all
- Endpoints can be missed in the assessment
- There can be a lapse between assessment and mitigation because of manual tasks
- Unsure how to prioritize all those vulnerabilities
- Reporting and tracking can be time-consuming
4 Simple Steps to a Successful Vulnerability Management Lifecycle
There are really just four key steps to a vulnerability assessment and management process. These are:
- Identify Vulnerabilities
- Prioritize Vulnerabilities
- Mitigate Vulnerabilities
- Document Vulnerabilities
These steps make up a lifecycle, where 1, 2, 3, and 4 are being done continuously to ensure that any new vulnerabilities continue to be detected and addressed.
Now, let’s take a look at how each of these steps works.
Step 1: Identify Vulnerabilities
Vulnerabilities need to be sought out and identified first. This involves doing an assessment of your entire network and all endpoints. This doesn’t have to be onerous if you automate the process.
Using a vulnerability assessment and management tool like CyberWizPro can significantly speed up the process and ensure all vulnerabilities are effectively identified.
CyberWizPro by WizNucleus
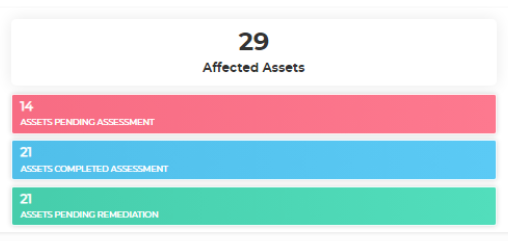
Once connected, the software can quickly scan all assets and report on the progress. Just ensure any new devices are added to the system when acquired and you can mitigate the risk of a vulnerability being missed because a device wasn’t scanned.
Step 2: Prioritize Vulnerabilities
The vulnerability prioritization process can hold up IT teams if they’re trying to prioritize hundreds of vulnerabilities manually. This can increase the time to remediation and leave an organization at risk.
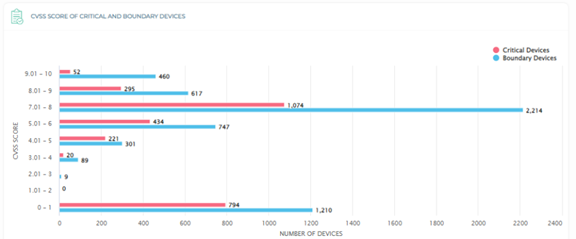
CyberWizPro takes the guesswork out of deciding which vulnerabilities need to be addressed first. It provides reporting on vulnerabilities both by the Common Vulnerability Scoring System (CVSS) score and the nature of the device. It will separate critical devices from boundary devices to help you quickly decide on a mitigation timeline.
Step 3: Mitigate Vulnerabilities
Mitigating vulnerabilities can be complex with a manual workflow. The IT team needs to identify the correct solutions and then deploy those to the asset. This is another process that can break down due to human error. For example, if two IT technicians each think the other handled a certain vulnerability and remediation tracking isn’t done efficiently.
When using the CyberWizPro tool, mitigation is as easy as reviewing the National Vulnerability Database (NVD) recommended remediation tactics provided by the software. It also lends visibility into security controls that have already been implemented, so the IT team isn’t doing unnecessary work.
These vulnerability-specific recommendations and insights streamline the mitigation process because you have all the data you need to move forward in front of you.
Step 4: Document Vulnerabilities
Documenting vulnerabilities and the steps taken to remediate them is important for compliance and cybersecurity activities. It informs future remediation and improves overall data security efforts because there is a log of what’s already been identified and handled.
Inspection-ready reports are generated automatically by the CyberWizPro system. This eliminates the need to spend hours in spreadsheets logging each vulnerability and remediation step. You can quickly generate an up-to-the-minute report anytime that includes all current vulnerabilities and where they are in the management lifecycle.
Because the process is automated, it can be running continually, identifying new vulnerabilities as others are being mitigated, so your organization has ongoing protection.
Are You Looking for an Easier Way to Manage Vulnerabilities?
Putting an effective vulnerability management process in place doesn’t have to be difficult when you use the right tools. CyberWizPro by WizNucleus can help you simplify and streamline so your IT team can focus on other mission-critical tasks.
CyberWizPro by WizNucleus can enable a strong vulnerability management program without all the traditional costs. Download a free trial today!

